-
Notifications
You must be signed in to change notification settings - Fork 29
Description
Project summary
Auto scale-to-zero pods when idle and scale up pods when traffic arrives, without losing any requests.
Project description
Problem Statement
Modern Kubernetes platforms waste up to 80% of resources on idle pods, and most scale-to-zero tools force code changes or risk reliability by being in the critical path.
About KubeElasti
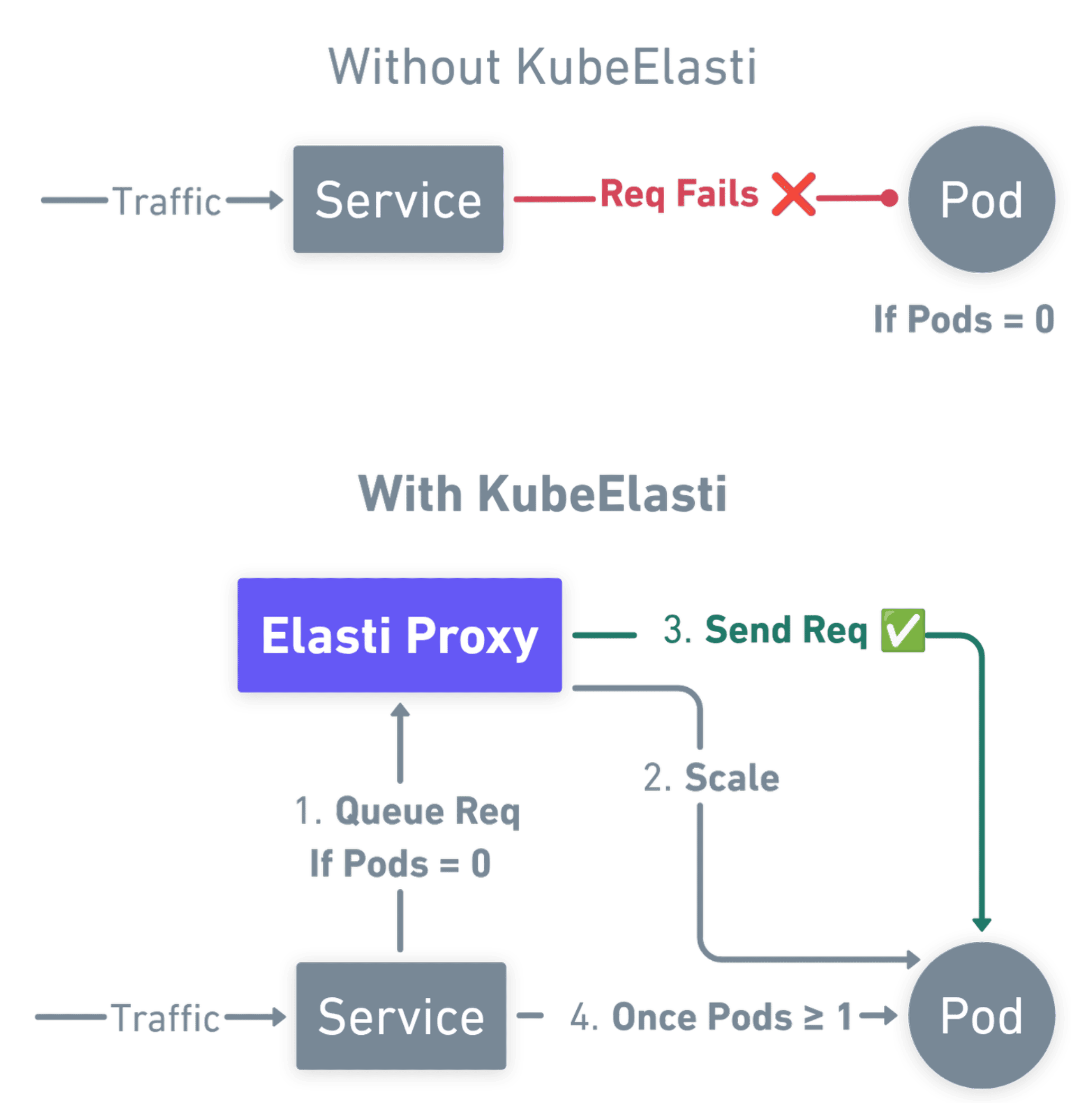
KubeElasti scales pods to zero when idle, and scales them up as traffic arrives, without losing any requests. It is easy to manage, doesn't require any changes in the existing infra, and removes itself from the hotpath when pods are scaled up.
How is it different?
- No need to rewrite services as functions: KubeElasti works natively with Kubernetes, works with existing services, deployments, etc. Just define the ElastiService CRD, which takes a
scale target referenceto enable scale-to-zero on it. - No added latency: KubeElasti uses a smart proxy, which is active only when there is no traffic. As traffic arrives, it queues the incoming requests, scales up the target, and resolves the queued requests. Once the pods are scaled up, traffic flows directly to the pods.
Other Features:
- It is ingress controller / service mesh agnostic.
- It supports any target/kind which supports a
/scalesubresource. - It integrates with HPA/KEDA for 1-to-N scaling.
- It comes with out-of-the-box monitoring using Prometheus.
How does it work?
KubeElasti is designed with simplicity in mind. It has two components:
- Controller: Monitors resources and scales them to 0 or N as needed.
- Resolver(Proxy): Intercepts incoming requests for scaled-down services, queues them, and notifies the controller to scale up the target.
There are two states for each service:
- Proxy Mode: When there is no traffic, redirect the traffic to the resolver.
- Serve Mode: When there is traffic, traffic flows directly to the pods.
graph LR
B[Ingress]
B -->|Traffic| C[Service]
subgraph Elasti Components
E[Elasti Controller]
F[Elasti Resolver]
F -->|Notify about traffic| E
end
C -->|"Proxy Mode(Pods = 0)"| F
E -->|Scale replicas to 0 -> N or N -> 0| D[Pod]
E -->|Poll configured metric every N seconds to check if the service can be scaled to 0| S[Prometheus]
C -.->|"Serve Mode(Pods > 0)"| D
Prometheus is used as a trigger to determine if a service can be scaled to zero, based on the traffic data.
Use Cases
- For development and testing environments where workloads are infrequently needed and receive sparse or intermittent traffic.
- For low traffic CPU workloads in production. Workloads that require small time to get provisioned.
Links
Org repo URL (provide if all repos under the org are in scope of the application)
N/A
Project repo URL in scope of application
Additional repos in scope of the application
No response
Website URL
Roadmap
Roadmap context
The current roadmap is mapped around new feature and enhancements, no stability related issues are open.
Contributing guide
https://github.com/truefoundry/KubeElasti/blob/main/CONTRIBUTING.md
Code of Conduct (CoC)
https://github.com/truefoundry/KubeElasti/blob/main/CODE_OF_CONDUCT.md
Adopters
https://kubeelasti.dev/src/adopters/
Maintainers file
https://github.com/truefoundry/KubeElasti/blob/main/MAINTAINERS
Security policy file
https://github.com/truefoundry/KubeElasti/blob/main/SECURITY.md
Standard or specification?
N/A
Business product or service to project separation
This project is unrelated to any product or service.
Why CNCF?
Why contribute KubeElasti to CNCF
CNCF can ensure governance, sustainability and community trust on KubeElasti. Moving under CNCF can help the project mature and scale its contributor and adopter base.
Value CNCF provides
CNCF gives credibility, visibility and access to the wider cloud-native community for KubeElasti. It can help set up the right guidance, legal/IP support and cross-project collaboration. That will help exponentially develop the project.
Why CNCF
The KubeElasti project already aligns with CNCF's mission to enable efficient, scalable, cloud-native infrastructure on Kubernetes. CNCF's focus on scale-to-zero complements existing CNCF autoscaling projects (like KEDA), fitting naturally into the ecosystem and adding real value.
Benefit to the landscape
Existing solutions like Knative, Keda, OpenFaaS, etc, require rewriting some or most of the infrastructure setup. KubeElasti seamlessly integrates with existing workloads without code changes, filling a key gap for users who wish to leverage serverless platforms within their existing cluster.
Cloud native 'fit'
KubeElasti fits under the Serverless – Installable Platforms category in the Cloud Native Landscape. It enables scale-to-zero and on-demand activation for Kubernetes workloads, delivering serverless behaviour on any cluster without external infrastructure.
KubeElasti follows core cloud native principles: elasticity and resource efficiency built directly on Kubernetes APIs. KubeElasti enables operational efficiency within existing Kubernetes environments.
Cloud native 'integration'
Depends on:
- Kubernetes: KubeElasti runs on Kuberenetes.
- Prometheus: Used to fetch traffic data to determine if a pod can be scaled down.
Complements:
- HPA/KEDA: KubeElasti handles the 0 -> 1 scale, and let's HPA or KEDA scale 1 -> N.
Cloud native overlap
We overlap with two projects from CNCF in the Serverless category. They both provide the scale-to-zero solution, with queued requests.
- KEDA HTTP Addon: The Key difference is that KubeElasti removes the proxy once the target is up, while KEDA HTTP Addon remains in the path.
- Knative: The Key difference is that KubeElasti doesn't require any rewrites, while Knative requires services to be deployed as Knative Services.
- Other FaaS Tools: Key difference is that they require a major rewrite, by asking to convert existing resources into functions. This is not the case with KubeElasti.
Here is a more detailed comparison: https://kubeelasti.dev/src/comp-main/
Similar projects
- The project has some scope overlap with KEDA HTTP Addon from CNCF Project https://keda.sh/
- https://knative.dev/
Landscape
N/A
Trademark and accounts
- If the project is accepted, I agree to donate all project trademarks and accounts to the CNCF
IP policy
- If the project is accepted, I agree the project will follow the CNCF IP Policy
Will the project require a license exception?
N/A
Project "Domain Technical Review"
We introduced the project on 1st October 2025, in TAG Workloads Foundation Community Meeting. Here are the meeting notes: https://notes.cncf.io/s/1aNdplhtl
We are presenting the project in the next meeting sometime in November, I will update the details here after that.
Application contact email(s)
[email protected], [email protected]
Contributing or sponsoring entity signatory information
If an organization:
| Name | Address | Type (e.g., Delaware corporation) | Signatory name and title | Email address |
|---|---|---|---|---|
| Ensemble Labs, Inc. | 355 BRYANT STREET, SUITE 403, SAN FRANCISCO, CALIFORNIA, 94107 | DELAWARE | Abhishek Choudhary, Chief Technical Officer | [email protected] |
CNCF contacts
No response
Additional information
No response
Metadata
Metadata
Assignees
Labels
Type
Projects
Status